Top Features For Endpoint Security Software
With the world getting extreme access to the internet for every little to big task, cyberattacks are becoming regular for any businesses that need severe action and strict protection. Endpoint security software offers security and protection to company devices from any threats and cyber attacks. Endpoint devices like laptops, smartphones, mobiles, and desktops can easily get malicious attacks and threats, and most of theft comes from these devices.
An endpoint security software not only safeguards network-connected devices, but it also performs as a centralized security solution by using antivirus, firewall, and anti-malware to detect and prevent malicious cyber attacks.
This article brings you detailed information on the top features for endpoint security software applicable to all sizes of organizations.
Top Endpoint Security Software Features
Anti-Exploit Technology
Anti-exploit technology mainly focuses on preventing attacks due to software vulnerabilities. It detects and blocks malicious code that arises to exploit software weaknesses within an application or an operating system. It monitors system processes, identifying suspicious behavior, protecting devices against known and unknown exploits and zero-day attacks. The anti-exploit technology offers a proactive approach, adding a crucial layer of defense as well as traditional antivirus software.
Benefits
- Protection against zero-day threats: The software offers protection against unknown attacks that are yet to occur, and that more dated antivirus tools may miss.
- Prevents attacks at the source: An endpoint security software blocks attacks or exploits at the source of an application or process level. It prevents threats from gaining any foothold in the system.
- Reduces risk: It alleviates breach risks, data theft, or malware spread by blocking malicious code before it acts.
Watchguard Endpoint Security
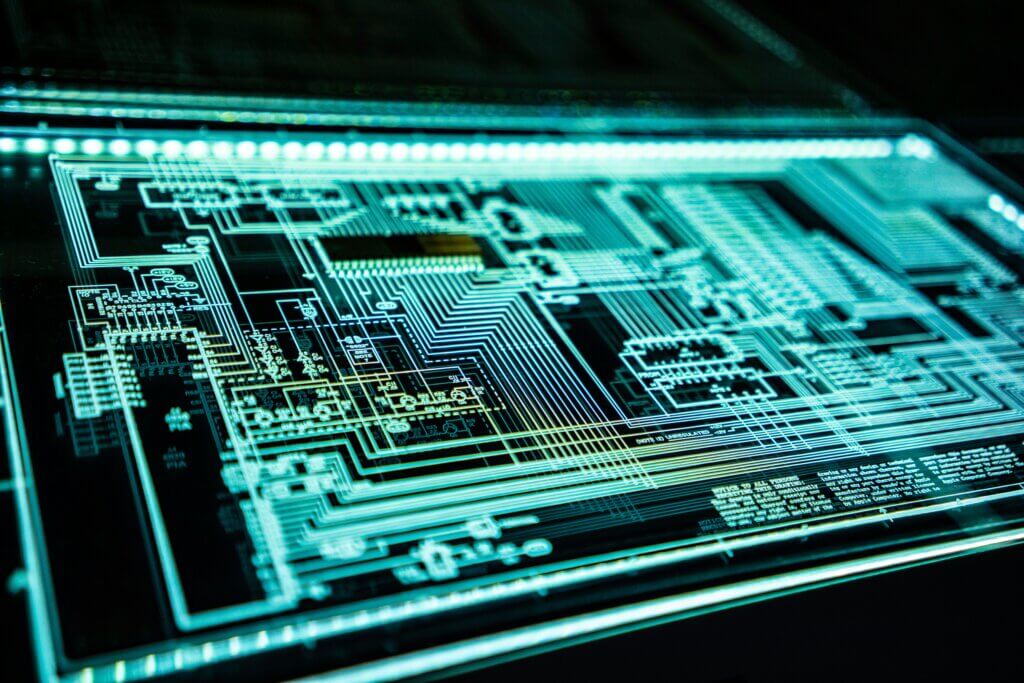
WatchGuard Endpoint Security offers a comprehensive suite of solutions that enables unified threat detection and automated response across diverse environments. Scalable for organizations of all sizes, from small businesses to large enterprises, this platform empowers proactive cybersecurity management in an increasingly complex digital landscape. Its users are particularly happy with its anti-exploit technology, rating the feature 8.8/10 in their TrustRadius reviews.
“We are a school with 220+ students and 45+ faculty members across 3 campuses. The WatchGuard Endpoint Security has eliminated any successful malware installations, which is our main focus on why we use it. The WatchGuard Endpoint Security protection has not hampered our network speed, and we are extremely happy with this product.”
Read James’ full review here.
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is a significant cybersecurity software that continuously monitors and records every activity on endpoint devices. It detects and responds to advanced threats. It also allows for comprehensive defenses by understanding malicious behavior and enabling easy and quick response to block sophisticated attacks.
Benefits
- Quick incident response: EDR generally automates actions and offers analysts the data required for rapid decision-making or taking action. It thus reduces the time it takes to fight against a threat.
- Precautions against advanced threats: With the help of behavioral analysis, EDR can detect unique attacks like fileless malware or zero-day exploits and take suitable precautions against them.
- Enhanced visibility: EDR offers security teams real-time visibility of all activities taking place on endpoints, leaving no blind spots.
- Proactive threat hunting: The software constantly collects data to enable security teams to actively hunt for hidden threats within their environment.
- Enhanced compliance: EDR can provide detailed logs and essential reporting for demonstrating compliance with regulatory requirements.
Microsoft Defender for Endpoint
Microsoft Defender for Endpoint (formerly Microsoft Defender ATP) is a holistic, cloud-based endpoint security solution that offers vulnerability management and assessment, attack surface reduction, behavior-based and cloud-powered next-generation protection, and endpoint detection and response (EDR). Happy Microsoft Defender for Endpoint users have scored the feature 9.1 in their TrustRadius reviews.
Centralized Management
Centralized management is one of the top features for endpoint security software that enables administrators to detect, control, and secure every endpoint from a single console. It ensures consistent policy enforcement and streamlined operations. Centralized management paves the way to unified visibility, automated tasks like deployment, patching, etc, and encourages faster incident response across a company’s networks, including hardware devices and servers.
Benefits
- Elevates efficiency: The management feature can streamline security operations and reduce workload for respective security teams.
- Increases security: This feature ensures the deployment of consistent security measures across every device of a company. Through that process, it reduces attacks and provides robust defense against a wide range of threats.
- Improved visibility: This feature gives users real-time visibility for all endpoints to make it easier to identify potential threats and vulnerabilities.
- Compliance: It facilitates companies to meet compliance requirements by rightfully obeying the security policies applied uniformly across all systems.
Cisco Secure Endpoint
Cisco Secure Endpoint offers security protection to a wide range of devices, like laptops, desktops, servers, mobile devices, and virtual workloads. With its centralized management supporting multi-factor authentication, customized views, and role-based access control, Cisco’s broader security architecture includes the Breach Protection Suite and User Protection Suite. Cisco Secure Endpoint users have scored this feature 8.2 in their TrustRadius reviews.
“With its multilayered protection, this tool protects all our devices from all manner of endpoint threats. We have deployed Cisco Secure Endpoint company-wide, and it helps keep cyberattacks at bay. From ransomware, malware, and data breaches, among other threats, this tool detects, responds, blocks, and reports all manner of threats, thereby keeping devices and systems optimal. It ensures proper visibility, and its proactive threat hunting makes it a better tool.”
Read Laurent’s full review here.
Hybrid Deployment Support
Hybrid deployment support in endpoint security software offers organizations to secure and manage endpoints across on-premises and cloud setups through a unified platform. A combination of traditional endpoint agents and agentless security devices, such as BYODs or cloud workloads, is used to achieve this support after creating a single security platform across a mixed IT infrastructure.
Benefits
- Unified platform: The feature offers a single platform to manage and enforce security policies across all the physical and virtual endpoints, irrespective of device location.
- Agentless security: Agentless methods can be used to scan, monitor, detect, and secure endpoints for workplaces like BYOD devices, cloud-based platforms, legacy systems, etc, where agents cannot be installed.
- Agent-based security: Under this approach, agents are installed across several corporate device endpoints for deeper control and quick threat protection.
- Policy enforcement: Consistent security policies must be enforced across every endpoint.
CrowdStrike Falcon
The CrowdStrike Falcon® platform combines a lightweight endpoint agent with an agentless cloud-native architecture to deliver real-time protection and visibility across your entire enterprise. It helps administrators choose endpoint security on-premise, cloud, or hybrid. Hybrid deployment helps companies to keep the workflow pace undisturbed through on-premises as well as cloud. The CrowdStrike Falcon users have scored the feature 8.2 in their TrustRadius reviews.
“We are a business associate to many healthcare organizations, and rely on ingesting ePHI data for our software. We absolutley need “best in class” threat protection and mitigation to protect not only our business, but the hospitals and other healthcare entities we serve. CrowdStrike Falcon complete absolutely protects us and our clients, and provides the visibility and peace of mind into our systems we are looking for.”
Read Dan’s full review here.
Infection Remediation
Infection remediation is the process of removing malicious code from endpoints once detected. These functions remove malicious files and their traces, isolate the infected device, patch obstructions, and restore the system to a secure form. Modern-day software automates all these steps to eliminate threats in real-time or roll back ransomware attacks.
Benefits
- Isolation: This feature can isolate the infected endpoint to block threats from spreading laterally to other devices across the network.
- Cleans and removes threats: The software cleans the infected file attacked at an endpoint and removes any residual threats from the system.
- Patching vulnerabilities: It identifies and applies required security patches as well as software updates to fix the vulnerabilities or obstructions that were exploited.
- Rollback ransomware attacks: For ransomware, advanced tools can reverse changes made by an attack by restoring files to their previous state.
ESET PROTECT
ESET PROTECT is a cloud-first XDR cybersecurity platform combining prevention, detection, and proactive threat hunting capabilities. It has the capability to quarantine infected endpoints and terminate malicious processes. ESET’s customizable solutions offer local support, boast minimal impact on performance, and identify and neutralize known and emerging threats before they are executed. ESET PROTECT users have scored the feature 8.8 in their TrustRadius reviews.
“We are using ESET PROTECT to centralize management of endpoint security devices. It is one type of web console that will be on cloud or on premises. Basically ESET PROTECT is an antivirus that protects endpoint devices. Also gives features like block USB devices, software firewall security, data encryption, and web-application filtering to block unwanted access.”
Read this Verified User’s full review here.
Vulnerability Management
Vulnerability management in an endpoint security software ensures a continuous process of identifying, prioritizing, assessing, and offering remedies for security blockages across hardware devices like laptops, desktops, smartphones, as well as servers. This integrates tools to scan vulnerabilities such as outdated software or misconfigurations. It also provides a structured approach to address the vulnerabilities through actions such as patching. This automatically reduces attacks and strengthens the entire network security.
Benefits
- Inventory: This process scans all devices on the network, and an endpoint security software integrates them with asset management systems for true visibility.
- Scanning and assessing vulnerabilities: The software proactively scans endpoints to detect security vulnerabilities. It also identifies and assesses outdated applications, unpatched systems, and misconfigured settings.
- Prioritizes Risk: It prioritizes detecting vulnerabilities or risks for any devices or networks that are being exploited and ensures those are addressed as a priority.
Bitdefender GravityZone
Bitdefender GravityZone takes care of vulnerability prioritization for fixes. Bitdefender GravityZone integrates endpoint protection, threat detection, and risk management into a unified platform, streamlining security operations and lowering infrastructure costs. Users of this product have scored the feature 10 in their TrustRadius reviews.
“We use Bitdefender as one of our managed antivirus options. It seems to pick up the things we need it to and offers an additional layer of protection in our security stack. We utilize it along with a firewall, phishing training, EDR, MDR, and several other pieces of security software.”
Read Joseph’s full review here.
Malware Detection
Endpoint security software employs signature-based and behavioral-based detection to identify all types of malware attacks. Signature-based detection matches files against a known malware database. Advanced methods include sandboxing in software that runs suspicious code in a virtual environment using predictive analysis to detect and prevent emerging threats.
Benefits
- Behavior-based detection: The software detects the real-time activity of every file and program. If a program shows suspicious actions like unauthorized access to sensitive data, it turns out to be a potential threat.
- Sandboxing: It transfers suspicious files to a safe and isolated virtual space in order to observe their behavior without disturbing the host device or the network.
- Dynamic analysis: Through static analysis, the software examines files, and then, through dynamic analysis like sandboxing, it observes how they perform.
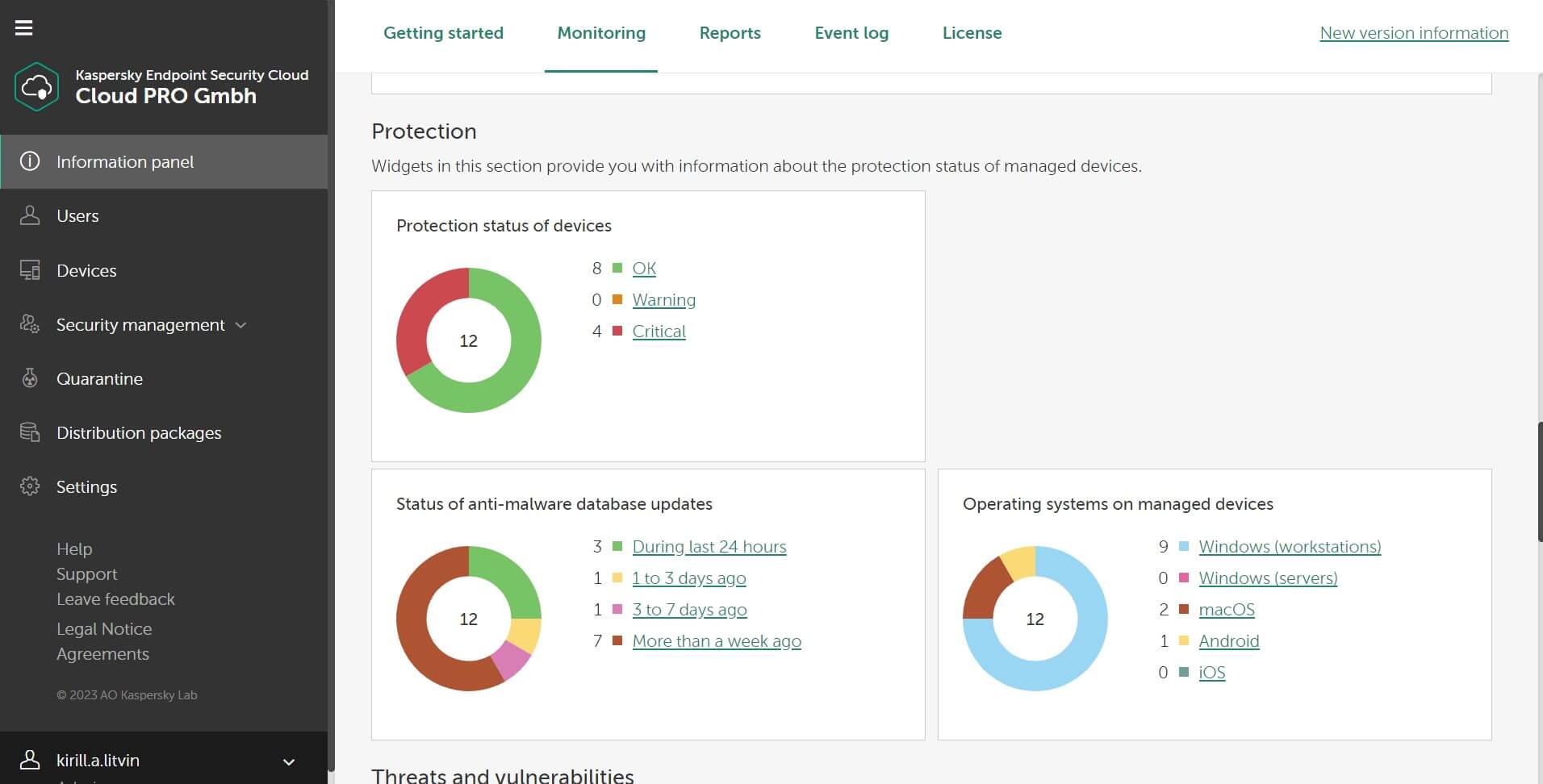
Kaspersky Endpoint Security Cloud
Kaspersky Endpoint Security Cloud offers detection and blocking of zero-day files and fileless malware. It provides a solution to organizations with IT security needs, blocking ransomware, file-less malware, zero-day attacks, and other emerging threats. Users have scored this feature 8.6 in their TrustRadius reviews.*
*Note: Kaspersky products are no longer available in the United States by order of the Department of Commerce. While they are still a well-known security vendor, proceed with caution. Click here to learn more.
Choosing the Top Features For Endpoint Security Software
An endpoint security software is significantly important for any business because it monitors, detects, and takes required measures against any cyber threats or malicious attacks taking place in devices or on the server. This software is crucial to employ for security or IT teams to keep the corporate system cyber threat-free. Considering the few top features for endpoint security software mentioned in this article, companies must ensure they buy the right ones that are suitable for their work environment, as well as cost-effective.
To continue your research, explore the Endpoint Security software on TrustRadius. You can compare products, read verified reviews, and see which solutions best fit your needs. You may also find value in related categories and resources, including: